downdimgd.com - Win32/DomaIQ Malware
I recently came across a website that would redirect users via an ad network to a site posing as a Java update page. The site as since been notified and fixed, but here are the details.
After sitting on a page for a little bit, the page would eventually redirect to a page that looked something like the page below (more details below). So you would be on a page you normally would visit, then in a few seconds, boom, you would be asked to install some malicious software!
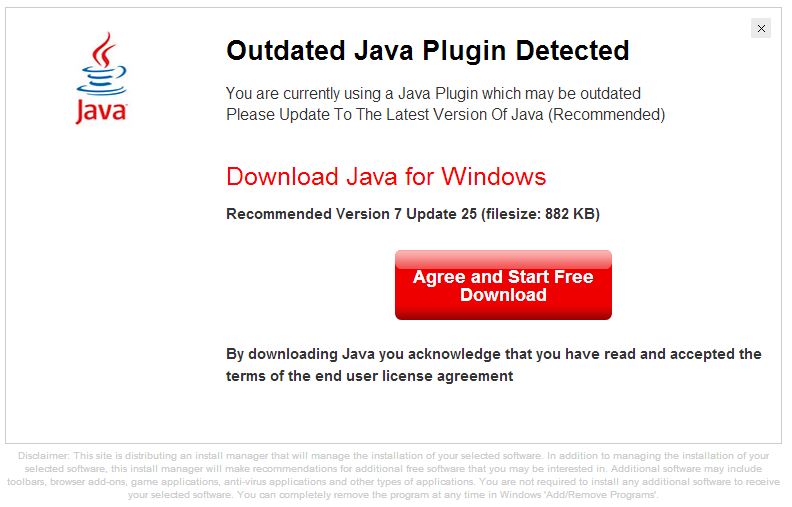 This page, would prompt the user to download and install a file called Java.exe. This file, after being scanned on virustotal.com, showed that it was a DomaIQ adware/malware variant.
This page, would prompt the user to download and install a file called Java.exe. This file, after being scanned on virustotal.com, showed that it was a DomaIQ adware/malware variant.
And now for the technical stuff...
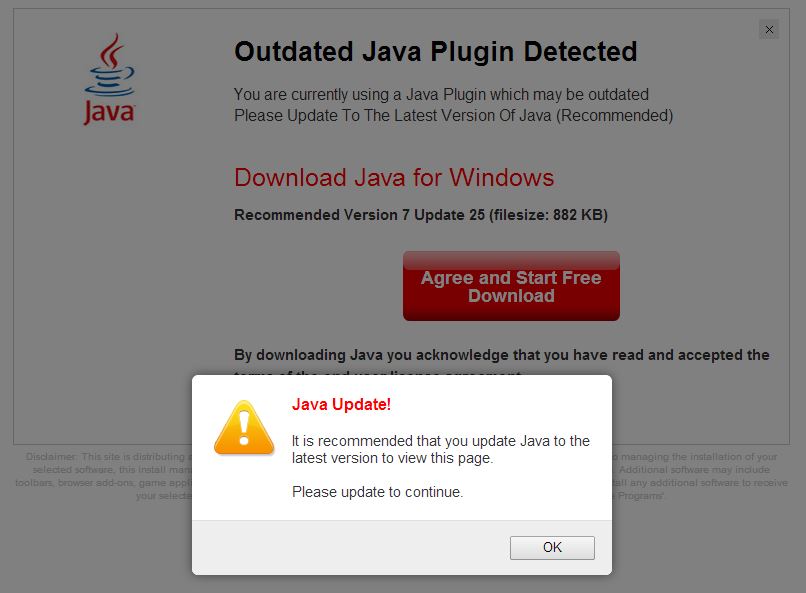
When you are first redirected to the page, there is a popup telling you that your Java version is out of date. When you click on OK, you are prompted to download a Java.exe application.
If you download the application you will see it is signed and valid to be run, the application is signed by Clovermedia SL.
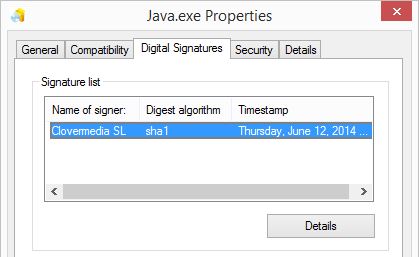
It looks like the file is very recent version of the application because the sign date is June 12, 2014 (the same day).
The hashes for the file are as follows:
For even more information on the file, visit the virustotal page, here.
If you look at the URL for the page, it is set to https://www.downdimgd.com. This was my telltale for it not being a real Java update on my initial viewing of the page.
The site appears to be hosted in Amsterdam (information listed below) but the name servers seem to be located in the US, by Namecheap, Inc. I have notified Namecheap of the malicious site.
Bottom line, if you are presented with a page like this, check the URL. Especially these days as more and more malware is being spread by fake sites. The same tactic is used to trick people to enter in bank login information, etc.
Checking the URL is ALWAYS the first line of defense. And if you are unsure about a website, odds are if it immediately tries to get you to download something it's probably malicious.
Be safe out there folks!
After sitting on a page for a little bit, the page would eventually redirect to a page that looked something like the page below (more details below). So you would be on a page you normally would visit, then in a few seconds, boom, you would be asked to install some malicious software!

| Avast | Win32:DomaIQ-CK [PUP] |
|---|---|
| ESET-NOD32 | a variant of Win32/DomaIQ.BB |
| F-Prot | W32/DomaIQ.C.gen!Eldorado |
| Kaspersky | not-a-virus:HEUR:AdWare.MSIL.DomaIQ.heur |
| Malwarebytes | PUP.Optional.DomaIQ |
| VIPRE | DomaIQ (fs) |
If you happened to actually run the installer and installed the malware, I recommend using Malwarebytes Anti-Malware to remove these types of nuisances. Malwarebytes offers a free version that you can use; check out their site, https://www.malwarebytes.org/ for more information.
And now for the technical stuff...
When you are first redirected to the page, there is a popup telling you that your Java version is out of date. When you click on OK, you are prompted to download a Java.exe application.

If you download the application you will see it is signed and valid to be run, the application is signed by Clovermedia SL.

It looks like the file is very recent version of the application because the sign date is June 12, 2014 (the same day).
The hashes for the file are as follows:
| MD5 | f0650efde761dfa8b02525606ea9a2f3 |
|---|---|
| SHA1 | 7650dddc3ea3454171b3e838381baa5a55bc8332 |
| SHA256 | 649e1a4f2afc69be56b96549650403e16ec28cd7035fff4e65b13da50df15e22 |
For even more information on the file, visit the virustotal page, here.
If you look at the URL for the page, it is set to https://www.downdimgd.com. This was my telltale for it not being a real Java update on my initial viewing of the page.
The full url is
Uri: www.downdimgd.com
Page: /US/index.php
Parameters:
dv1=10523998
dv2=
dv3=
dv4=zqsye-US
sec_id=qWJ8vBQjIEzEzreaz9tov0poz3iSC9s6Y3RmIaRrCnYR7BX87cCKqZsRNasrPBw0DlpefAXdNauePw%EB%EB
marketing_fid=MTQwMjYxOTc4Mi02ZTcwNDM0ODAyNGM5OThlNzc2ZGY2YzRjYjJlMzU0Zg==
The site appears to be hosted in Amsterdam (information listed below) but the name servers seem to be located in the US, by Namecheap, Inc. I have notified Namecheap of the malicious site.
inetnum: 91.218.112.0 - 91.218.115.255
netname: BERMOSCOM-NET
descr: BerMosCom GmbH
country: RU
org: ORG-BG35-RIPE
admin-c: ANSH13-RIPE
tech-c: ANSH13-RIPE
status: ASSIGNED PI
mnt-by: RIPE-NCC-END-MNT
mnt-lower: RIPE-NCC-END-MNT
mnt-by: BERMOSCOM-MNT
mnt-routes: BERMOSCOM-MNT
mnt-domains: BERMOSCOM-MNT
source: RIPE # Filtered
organisation: ORG-BG35-RIPE
org-name: BerMosCom GmbH
org-type: OTHER
address: Siegfriedstr. 49-60
address: 10365 Berlin, Germany
mnt-ref: BERMOSCOM-MNT
mnt-by: BERMOSCOM-MNT
source: RIPE # Filtered
person: Andrey Shevchenko
address: Mir Telematiki
address: 19/2 Lva Tolstogo st.
address: Moscow 119034
address: Russia
abuse-mailbox: [email protected]
phone: +7(499)2463587
nic-hdl: ANSH13-RIPE
mnt-by: MTLM-MNT
source: RIPE # Filtered
route: 91.218.115.0/24
descr: BermosCOD
origin: AS49335
mnt-by: BERMOSCOM-MNT
source: RIPE # Filtered
Bottom line, if you are presented with a page like this, check the URL. Especially these days as more and more malware is being spread by fake sites. The same tactic is used to trick people to enter in bank login information, etc.
Checking the URL is ALWAYS the first line of defense. And if you are unsure about a website, odds are if it immediately tries to get you to download something it's probably malicious.
Be safe out there folks!